Maritime Cyber Security
Remote internal/external Vulnerability & Penetration Testing
Industry Regulations-Guidelines
-IMO MSC-FAL.1/Circ.3
-The Guidelines on Cyber Security Onboard Ships
Version 4 (BIMCO-INTERTANKO-OCIMF-ICS-SYBASS-WSC)
-USCG Office of Commercial Vessel Compliance CVC-WI-027(1)
Maritime Sectors
-Dry Bulk Management Standard
-TMSA 3 Requirement , Vessel Inspection Questionnaire (VIQ)
This IMO circular refers to several standards to help identify and mitigate cyber risks, including five functional elements consistent with the NIST Framework:
a. Identify: Define personnel roles and responsibilities for cyber risk management and identify the systems, assets, data and capabilities that, when disrupted, post risks to ship operations.
b. Protect: Implement risk control processes and measures, and contingency planning to protect against cybersecurity events and ensure continuity of shipping operations.
c. Detect: Develop and implement activities necessary to detect a cybersecurity event in a timely manner.
d. Respond: Develop and implement activities and plans to provide resilience and to restore systems necessary for shipping operations or services impaired due to a cyber-event.
e. Recover: Identify measures to back-up and restore cyber systems necessary for shipping operations impacted by a cybersecurity event.
Cyber-technologies have become essential to the operation and management of
numerous systems critical to the safety and security of shipping and protection of the marine
environment. In some cases, these systems are to comply with international standards and
Flag Administration requirements. However, the vulnerabilities created by accessing,
interconnecting or networking these systems can lead to cyber risks which should be
addressed. Vulnerable systems could include, but are not limited to:.
1 Bridge systems;
.2 Cargo handling and management systems;
.3 Propulsion and machinery management and power control systems;
.4 Access control systems;
.5 Passenger servicing and management systems;
.6 Passenger facing public networks;
.7 Administrative and crew welfare systems; and
.8 Communication systems.
Ship operators will need to include cyber in ship safety and security management under the ISM Code from
1 January 2021
This came into force on 1 January this year, with a new element on maritime security and additional requirements of key performance indicators and risk assessments.
DOWNLOAD VARIOUS GUIDELINES:
IMO – GUIDELINES ON MARITIME CYBER RISK MANAGEMENT MSC-FAL.1/Circ.3:
 IMO MSC-FAL.1-Circ.3 (94.7 KiB, 1,637 hits)
IMO MSC-FAL.1-Circ.3 (94.7 KiB, 1,637 hits)
USCG Office of Commercial Vessel Compliance (CG-CVC)
Mission Management System (MMS) Work Instruction (WI)
 USCG – USCG-CVC-WI-027 (985.8 KiB, 1,500 hits)
USCG – USCG-CVC-WI-027 (985.8 KiB, 1,500 hits)
BIMCO – THE GUIDELINES ON
CYBER SECURITY ONBOARD SHIPS Version 4
 BIMCO (3.4 MiB, 1,572 hits)
BIMCO (3.4 MiB, 1,572 hits)
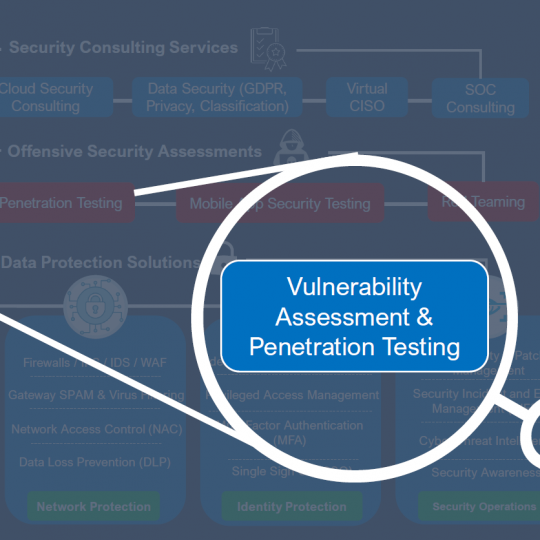
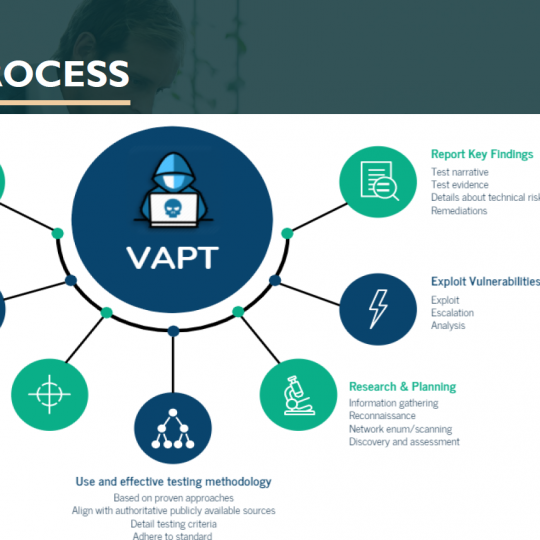
Penetration test
Penetration testing looks at vulnerabilities and will try and exploit them. The testing is often stopped when the objective is achieved, i.e. when an access to a network has been gained – this means there can be other exploitable vulnerabilities not tested.
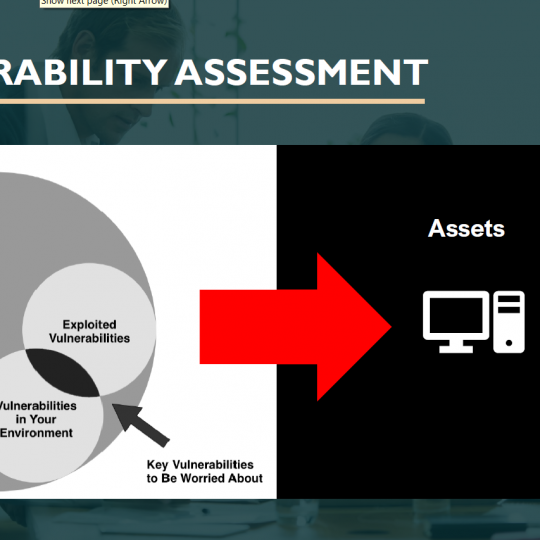
Vulnerability tEST
A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
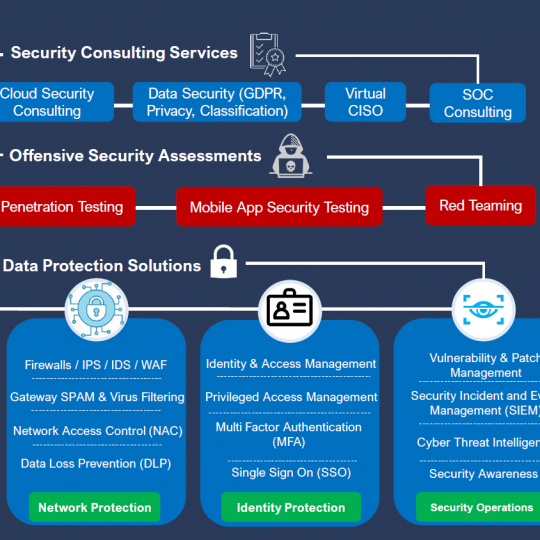
SHIP IP LTD – with our global network of certified engineers will help your company to complete and maintain a risk assessment for your offices and fleet going through a 3rd party Vulnerability and Penetration Test to your Systems.
Following the assessment, each identified vulnerability should be evaluated for its potential impact and the probability of its exploitation.
Recommended technical and/or procedural corrective actions should be identified for each vulnerability in a final report.