Tanker management self-assessment (TMSA) may be voluntary in principle but for tanker operators seeking regular charters from oil majors meeting its requirements is a fundamental commercial imperative.
Whereas traditional class requirements give a snapshot of a vessel’s quality at a given moment in time, TMSA was devised to gauge quality of a company’s operations over time. The second edition of the programme, which was introduced in 2008, comprised twelve elements covering a range of safety and performance metrics. In April last year, OCIMF, the industry body that devised and maintains the assessment programme, released a highly anticipated update, that took effect from 1 January 2018.
The update from TMSA2 to TMSA3 was a radical overhaul. The biggest change was the introduction of a completely new element on maritime security that zeroed in on cyber risk management. “While there was a growing awareness of cyber risk in the shipping industry, until that point it was nearly always framed in the future tense. It was raised as a hypothetical issue, one that would have to be addressed in the years to come,” observes Jason Stefanatos, Senior Research Engineer in DNV GL’s Maritime R&D and Advisory team. “Offering operators less than a year to prepare or risk losing business, TMSA3 brought it solidly into the present.”
Holistic approach
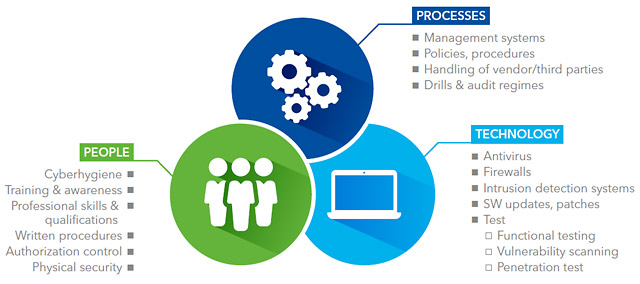
Effective cyber security is built on three pillars: people, processes and technology. “There’s still a common misconception that it’s a matter for the company IT department and that as long as I remember my password, it doesn’t affect me. But that’s no longer today’s reality,” Stefanatos stresses.
IT departments do play an important role in implementing technical mitigations such as firewalls and intrusion detection systems and so forth, and it is true these defences successfully prevent many attempted attacks. However, processes are also essential. “End-users – both crews at sea and staff ashore – need to know how to react to the attack or system failure that wasn’t prevented or anticipated by technical safeguards,” he warns. More importantly, he adds: “You need people to be aware of the risks and to take them seriously.”
TMSA3’s new maritime security section – Element 13 – is intended to instil these behaviours and encourage operators to adopt such a holistic approach. To attain the lowest score (Level 1), procedures for identifying threats applicable to the vessel and shore sites must be demonstrated. Reaching Level 2 requires guidance and mitigation measures in all procedures, as well as the promotion of cyber security good-practice among vessel personnel. Satisfying Level 3 calls for security procedures to be regularly updated. The highest grade, Level 4, demands that novel or innovative methods for minimizing cyber risk are evidenced.
Leadership and change
Although cyberrisk management is addressed in greatest depth in Element 13, it exerts a gravitational pull on other elements covered by TMSA. Providing an effective response to cyberrisk, for instance, will require good leadership (Element 1). Meanwhile, management of change (MoC, Element 7) will have to incorporate software and system configuration management. The latter aspect is particularly important.
Satisfying Level 1 of MoC requires that documented procedures are in place for implementing change and for assessing its impact, as well as specifying the framework for granting approval. Level 2 demands that all documentation and records affected by the change are identified and amended or annotated.
Reaching Level 3 calls for a comprehensive software management procedure covering both shipboard and shore systems. Crucially this goes beyond items typically associated with standard business IT infrastructure and should include operational technology (OT), such as the PLCs (Programmable Logic Controllers) and related interfaces for controlling onboard machinery.
Threat evolution
The threat landscape is evolving faster than ever, says Stefanatos. Hackers have grown up and become professional. They are more organized and have more resources at their disposal. Consequently, techniques and tactics have grown in sophistication.
In the 2000s, office IT systems were the predominant target. In other words, the PC on your desk. But these days, attacks directed at OT – the embedded systems and PLCs – are growing increasingly frequent. “It’s a worrying trend. Whereas before it was mostly a company’s finances and reputation at risk, now that has escalated to safety of life, property and the environment. The stakes are much higher,” Stefanatos observes.
One of the first obstacles facing any operator implementing the new TMSA requirements is to decipher and establish a common interpretation of what they mean, a task which, according to Stefanatos, isn’t as straightforward as it sounds: “Some are open to interpretation depending on what perspective you’re approaching them from. Senior managers, for example, may arrive at different conclusions to those working in the IT department or working as an ETO on a ship. It is essential everyone agrees before getting started.”
Demanding work
Another challenge is the sheer amount of work involved in performing the necessary risk assessments for all IT and OT systems. “Because the procedures and documentation are new, they must be created from scratch. Tanker owners are familiar with how TMSA works, but few quite anticipated the scale of the task facing them,” explains Stefanatos recalling conversations with clients.
Operators can purchase pro forma procedures off the shelf, but he emphatically cautions against taking such shortcuts: “A cookie-cutter approach defeats the object. Unless you properly investigate and drill down into the potential security gaps particular to your company, you won’t be able to find the vulnerabilities specific to your operations. In turn, you won’t be able to devise effective remedial actions or countermeasures.”
GET THE SAFETY4SEA IN YOUR INBOX!
While the workload might be daunting, ultimately managing cyber risk is no different to managing any other risk. The equipment and terminology may be unfamiliar but the approach is fundamentally the same as, say, managing any hot work that modifies a vessel’s structure. Software changes, for example, should not be done ad hoc. They should be planned, approved, and recorded. They should be categorized as minor or major to ensure personnel with appropriate authority can approve. This is very similar to the process for gaining approval prior to carrying out welding.
Close collaboration
In 2016, DNV GL compiled and published a set of recommended practice (RP), which details the principles and processes that underpin effective cyber risk management. It provides an authoritative resource for operators of tankers – or any ship type – intending to build a cyber risk management system under their own steam.
However, feedback from and conversations with tanker operators using the RP highlighted a clear need for a more collaborative approach. “Operators understood the guidance as it was written down on paper but translating that into action was proving harder than expected,” notes Stefanatos. This realization prompted DNV GL to start providing dedicated advisory services to assist operators meet TMSA3 requirements.
DNV GL experts work alongside the operator to familiarize themselves with the existing management system and then carry out a gap analysis. This reveals what safeguards are already in place, what requires attention and what’s missing. These outcomes facilitate a highly methodical approach to developing procedures that are effective at reducing risk and that mesh neatly with the specific nuances of an operator’s structure and working practices.
The final stage is for the procedures to be tested to ensure that all the identified gaps have been addressed and that they would stand up under the scrutiny of a TMSA vetting inspection. Depending on the level of customer engagement, the whole process can take between six and eight weeks to complete.
Positive feedback
With only a short window of opportunity between TMSA3 being announced and it taking effect, DNV GL has experienced strong uptake for its advisory services from across the tanker segment, including a number of reputed Greek operators.
Frantzeskos Kontos, Technical Manager at Prime Marine Management, says cyber security is no longer a paperwork exercise. “In recent times, we’ve identified many minor threats – and a handful of more serious ones – on our vessels, so it was urgent we took action to prevent further escalation. The inclusion of cyber security in TMSA gave us an additional commercial impetus.”
Collaborating with DNV GL enabled the Greek operator to detect gaps existing in its management system and address them swiftly and systematically. Procedures were enhanced and new control measures were introduced as a direct result of DNV GL’s proposals and recommendations. “There were some challenging discussions along the way, but, on reflection, they produced tangible results,” reports Kontos.
Initially educating and bringing employees on board was challenging, Kontos admits. “DNV GL’s training resources proved effective in communicating the criticality of cyber security to staff at all levels and across company operations, on shore and at sea.”
Minerva Marine also turned to DNV GL to help it develop a cyber resilience strategy that both complies with TMSA3 and aligns with forthcoming IMO requirements. Part of the project was to carry out a vulnerability assessment on board a Minerva vessel. Company IT manager Eftihia Benaki says: “In addition to the potential financial and reputational damage, cyber risk now carries significant safety and environmental implications. The assessment was invaluable in revealing the technical gaps we faced and identifying the areas we needed to focus on.” She adds: “DNV GL provided a depth of resource and level of specialism that we didn’t have internally.”
The Massachusetts Institute of Technology (MIT) calls cyber security a negative target: it is impossible to ever be 100 per cent secure. This is for two reasons. Firstly, it’s highly dynamic with new threats and risks emerging on a daily basis and, secondly, there is a large attack surface for hackers to exploit. This latter aspect is especially true in a complex supply chain environment, such as shipping, characterized by interactions with and between numerous and diverse stakeholders. However, as we have seen, it is possible to take steps and minimize exposure to these risks and plan a response for when the unexpected happens. This is what TMSA3 essentially seeks to achieve by incentivizing preparedness.
While TMSA3 has made cyber risk management a priority for tanker operators, it is only a matter of time before similar requirements arrive in other market segments. The advisory services developed by DNV GL for TMSA3 sit alongside with associated cyber security offerings including gap analysis for various global standards; a growing range of practical services including penetration testing and incident response drills; and training courses for raising awareness and tackling phishing and social engineering. These can be deployed in various configurations to manage risk on bulk carriers – should RightShip evolve in this direction – and across the global fleet when IMO requirements to incorporate cyber risk within ISM take effect in 2020.
Reflecting on the maritime industry’s response to cyber risk has evolved, Stefanatos observes: “Misha Glenny, a British computer journalist specializing in cyber security, famously quipped that there are two types of companies in the world: those that know they’ve been hacked and those that don’t. Maybe the day has come to add a third type: those that have prepared and are confident they can respond.”
Source: safety4sea