The Coronavirus pandemic is leaving the maritime and offshore energy sectors vulnerable to cyber-attack, with Naval Dome citing a massive 400% increase in attempted hacks since February 2020.
While an increase in malware, ransomware and phishing emails exploiting the Covid19 crisis is the primary reason behind the spike, Naval Dome furthers that travel restrictions, social distancing measures and economic recession are beginning to bite into a company’s ability to sufficiently protect itself.
Naval Dome CEO Itai Sela said: “Covid-19 social restrictions and border closures have forced OEMs, technicians, and vendors to connect standalone systems to the internet in order to service them.”
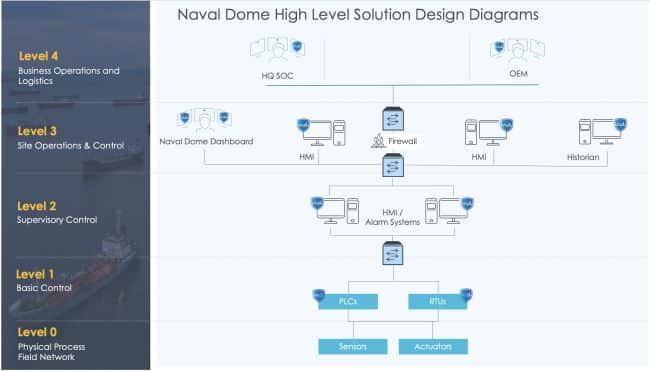
Image Credits: seabornecomms.com
The global crisis and social distancing measures are preventing OEM technicians flying out to ships and rigs to upgrade and service critical OT systems, resulting in operators circumventing established security protocols, leaving them open to attack.
“As budgets are cut and in the absence of service engineers, we are seeing ship and offshore rig staff connecting their OT systems to shoreside networks, at the behest of OEMs, for brief periods of time to carry out diagnostics and upload software updates and patches themselves.
This means that their IT and OT systems are no longer segregated and individual endpoints, critical systems and components may be susceptible. Some of these are legacy systems which have no security update patches and are even more susceptible to cyber attack.
“The increase in OEM personnel working remotely on home networks and personal PCs, which are not well protected, adds to the problem.”
Sela said that during the first three months of 2020, attacks targeting home workers increased tenfold, adding that PC security software provider McAfee has reported that that between January and April cloud-based cyber-attached on all businesses increase by 630%.
He furthered that the economic downturn and the drop in the price of crude oil is also having an effect, with oil companies and contractors being faced with limited budgets available to implement effective cyber security measures.
“Companies are stretched thin and this is benefitting the hacker,” said Sela.
“It is not sufficient to protect only networks from attack,” said Sela. “Each individual system must be protected. If networks are penetrated, then all connected systems will be infected.
“Our philosophy is that all systems must be protected using a risk ranking. If it is, then the entire platform is protected from both internal and external attack vectors. If only the network is protected, then whatever enters the net (such as an unintentional attack from authorised personnel) will infect all connected systems. This philosophy is more cost-effective.”
Naval Dome’s software solutions adhere to the strict cyber security protocols set by the National Institute of Standards and Technology (NIST).
NIST’s Purdue Model for industrial control systems and architecture – an industry adopted reference model that shows the interconnections and interdependencies of all the main components of a typical inter-connected systems – divides ICS architecture into three zones and six levels. Naval Dome protects more deeply embedded systems such as HMIs, alarm/alert and control room workstations to NIST Level 1 and above.
The Purdue Model allows information security professionals and process control engineers that are responsible for protecting an organization’s most valuable assets to visualize how to protect against a security breach, whether involving confidentiality, integrity and/or availability.
Ido Ben-Moshe, Vice President Business Development, said the problem is particularly acute in the marine and offshore oil and gas sectors. “If hackers penetrate networks, and critical equipment is exposed there could be significant safety, downtime, financial and potential reputational damage.
Ben-Moshe added that remote working and the introduction of remotely controlled, autonomous technologies is likely to take place at a faster pace in a post-coronavirus world.
“This will see companies face new cyber security challenges if they fail to implement adequate protective measures,” he said.
Source: https://www.marineinsight.com/







