Maritime cyber risk management: boiling the ocean or storm in a tea cup?
May 16, 2019 BIMCOCONSULTANCYCYBER SECURITYIMOMARITIME CYBER SECURITYMaritime Safety News
Maritime cyber risk management: boiling the ocean or storm in a tea cup?
Is the shipping industry’s most valuable commodity also its biggest risk?
As one of the world’s oldest industries, the shipping industry has capitalised on its capability to move assets around the world for thousands of years. Whether for trade, military or tourism, there are more than 50,000 ships world-wide that currently navigate our waters and facilitate both thriving economies and promote nation state security.
Know your risks and implement security measures
Our recent maritime report has explored the cyber security challenges that the maritime industry is facing now and will likely face in the future. With the increasing trend of attackers turning their attention to ships and shipping operations, more needs to be done to identify cyber risks at sea and mitigate them – a method to begin this process is to perform a risk assessment. Traditionally, a business might perform a risk-assessment periodically, say on a yearly basis, to identify what security risks need addressing, and follow this with implementing the right measures to protect against these risks occurring.
But what happens when your risk profile is constantly changing? All variables such as a ship’s cargo, employees and geography can change drastically within 24 hours as a ship makes its journey across the world and participates in trading. The main inputs to assessing risk are therefore constantly changing, significantly more than your standard business who needs to implement cyber security measures – so how is it feasible to have confidence that ships are implementing the right security in such a unique situation?
What are the key changing risk factors?
We have identified the main factors impacting cyber security that are associated with the constant movement of trade ships as follows:
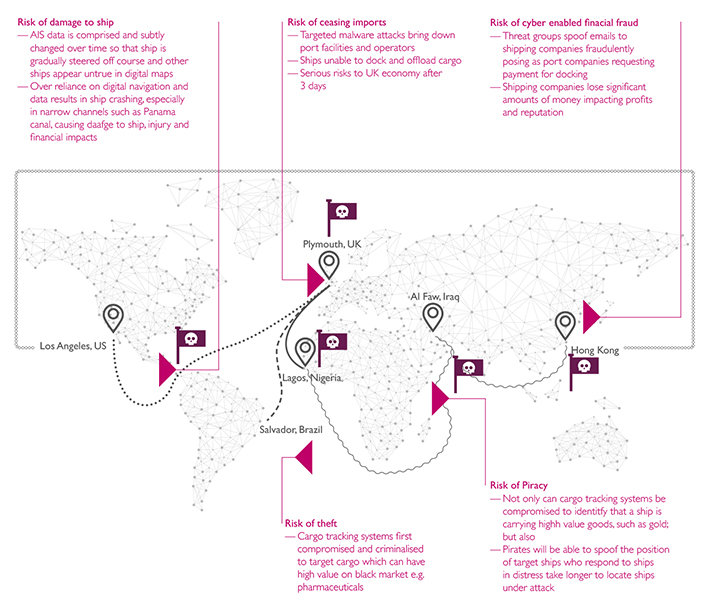
- Route: A ship relies on multiple navigation technologies to get it safely from point A to point B without damaging it, its cargo or risking life onboard. But what if malware could ever so slightly change measurements over time, à la Stuxnet. This would have little impact in the Pacific; but in the Panama Strait it would be catastrophic and the perfect attack for criminals to launch in order to then loot a ship.
- Cargo: A ship will be carrying multiple cargos of different market value during its route and over time. These cargos may also have different value to different territories and groups. Cargo systems can be compromised providing intelligence to criminals who can subsequently target specific cargo ships and resell on the black market. For example, pharmaceuticals would be an attractive target due their high value on the black market.
- Piracy: There are certain areas of the world which may be at higher risk of attack from piracy, such as the seas that border Eastern Africa. Not only could the cargo training systems be tracked to identify when ships are carrying precious cargo like gold; we understand that pirates could also manipulate systems and spoof the position of ships in distress. This would result in a longer period of time for them to carry out their physical attacks.
- Ports and business operations: Shipping staff may engage with multiple ports and succumb to various operational processes each time, notably payment and administration regarding docking. Threat groups have been known to track ships and spoof emails to shipping companies to request payment for their upcoming or previous docking. This has resulted in ships losing money as they have been unable to distinguish what is the legitimate process for these payments – made harder when a ship uses many ports over a short period of time.





